RivicID: Quantum-Safe Identity Management
The foundation of secure digital identity with quantum-resistant cryptography, zero-knowledge proofs, and seamless cross-chain compatibility.
Next-Generation Digital Identity
RivicID provides a comprehensive quantum-safe identity management solution that maintains the highest levels of security while ensuring complete privacy and sovereignty over personal data. Built on post-quantum cryptographic primitives, RivicID enables secure authentication across decentralized applications, financial services, and enterprise systems.
Unlike traditional identity solutions, RivicID stores private keys in secure hardware security modules (HSMs) while using zero-knowledge proofs for verification, eliminating the risk of data exposure during authentication processes.
Core Technologies
Post-Quantum Cryptography
RivicID implements lattice-based cryptographic algorithms that are resistant to quantum computing attacks. Our implementation of CRYSTALS-Dilithium provides digital signatures that remain secure in the post-quantum era, while CRYSTALS-Kyber enables secure key encapsulation mechanisms.
Zero-Knowledge Authentication
Our proprietary ZK-STARK implementation enables users to prove possession of identity credentials without revealing the actual data. This zero-knowledge approach allows for selective disclosure of identity attributes while maintaining cryptographic verifiability and complete privacy.
Secure Hardware Integration
RivicID leverages hardware security modules (HSMs) and secure enclaves to store private keys in tamper-resistant environments. Our architecture ensures that cryptographic operations occur within secure hardware boundaries, preventing key extraction even in compromised systems.
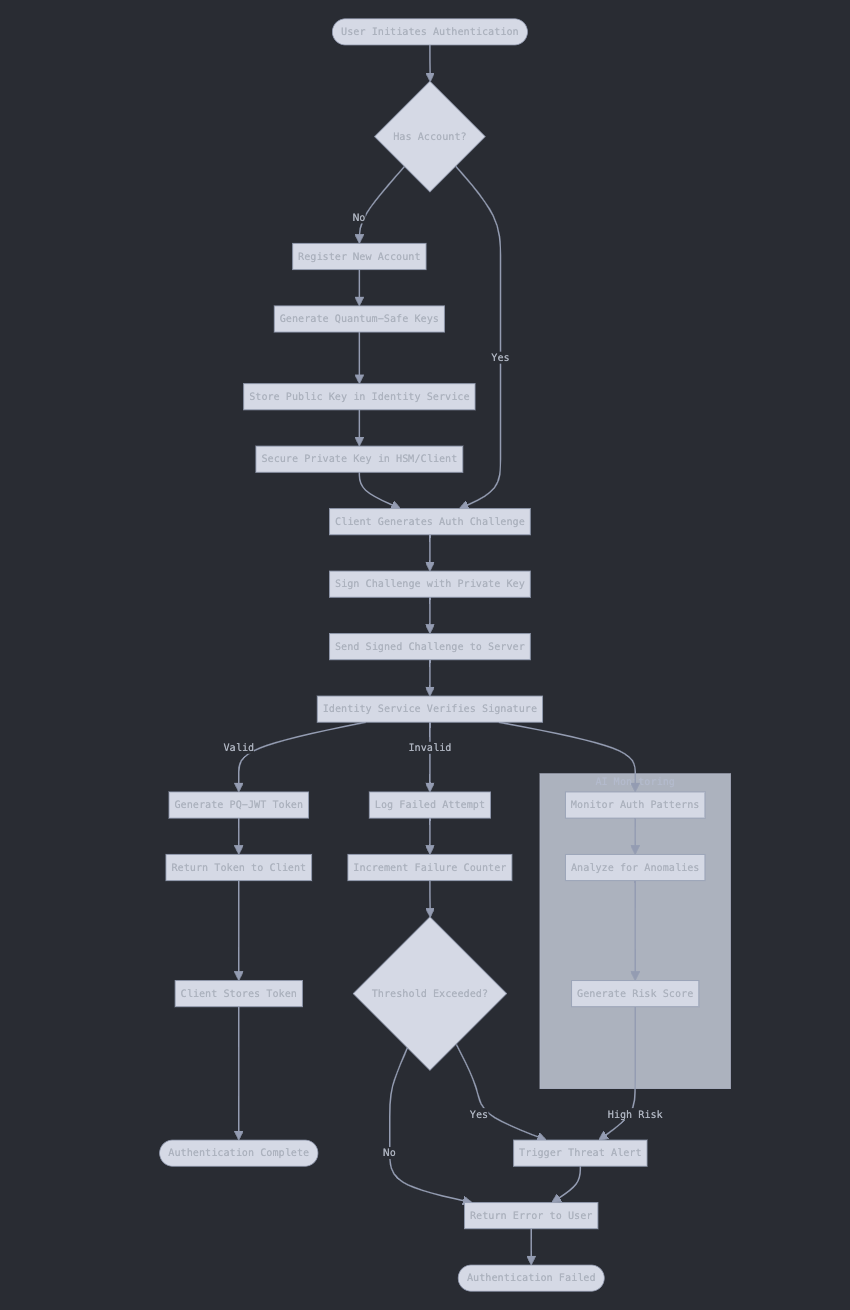
Operational Mechanism
- Quantum-Safe Key Generation: During account creation, RivicID generates quantum-resistant key pairs using lattice-based cryptography. The private key is securely stored in an HSM or secure enclave, while the public key is registered with the Rivic Identity Service.
- Challenge-Response Authentication: When authentication is requested, the client generates a cryptographic challenge. This challenge is signed using the private key stored in the secure hardware, creating a quantum-resistant signature that proves identity possession without exposing sensitive data.
- Zero-Knowledge Verification: For attribute verification, RivicID generates zero-knowledge proofs that allow specific identity claims to be verified without revealing the underlying data. This enables selective disclosure of information.
- Cross-Chain Propagation: Identity attestations and verifiable credentials are anchored across multiple blockchains through the Rivic Chain Adapter, ensuring consistent identity representation across the decentralized ecosystem.
- Continuous Security Monitoring: RivicID integrates with SentinelX to continuously monitor authentication patterns, analyzing behavioral biometrics and contextual factors to detect anomalies and prevent unauthorized access attempts.

Ecosystem Integration
Financial Services Integration
RivicID provides standardized interfaces for KYC/AML compliance while preserving user privacy. Financial institutions can verify identity attributes through zero-knowledge proofs without accessing raw personal data.
The system facilitates secure access to DeFi protocols and cross-border payment systems while maintaining compliance with regulatory requirements and preventing identity fraud.
Enterprise Identity Framework
For enterprise deployments, RivicID integrates with existing identity infrastructure through SAML, OAuth, and OIDC adapters, providing a seamless migration path to quantum-safe authentication.
The enterprise framework includes role-based access controls, security policy enforcement, and comprehensive audit logs for governance and compliance requirements.
Key Benefits
Quantum-Resistant Security
Future-proof your identity infrastructure against advances in quantum computing with post-quantum cryptographic algorithms.
Complete Data Privacy
Zero-knowledge proofs enable authentication and verification without exposing underlying personal data, ensuring complete privacy.
Cross-Chain Identity
Maintain consistent identity representation across multiple blockchains and decentralized applications without fragmentation.
Regulatory Compliance
Satisfy KYC/AML requirements while preserving user privacy through selective disclosure and verifiable credentials.
Hardware-Level Security
Private keys remain secured in tamper-resistant hardware, eliminating the risk of extraction even if the host system is compromised.
Seamless Authentication
User-friendly authentication experience with enhanced security through hardware integration and AI-powered behavioral monitoring.